Article overview
Traditional networking is difficult—it involves equipment, cabling, complex configurations, and specialist skills. Fortunately, Amazon Virtual Private Cloud (Amazon VPC) hides the complexity while making it easy to deploy secure private networks.
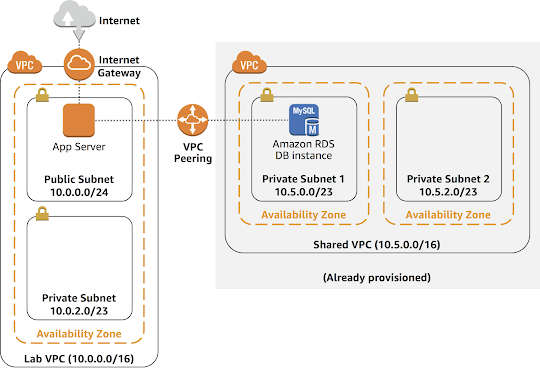
This lab shows you how to build your own VPC, create subnets, and direct traffic between VPC components. The following image shows the final architecture:
An optional Challenge task is available. In the challenge task, you create a VPC peering connection to a shared services VPC. Then, you use an application and database to test connectivity between the VPCs.
Objectives
After completing this lab, you will be able to:
Create a VPC
Create public and private subnets
Create an internet gateway
Configure a route table and associate it to a subnet
Article Process Duration
This Article Procedure requires approximately 30 minutes to complete.
Common Login ErrorsError: You must first log out

If you see the message, You must first log out before logging into a different AWS account:
- Choose click here
- Close your browser tab to return to your initial Article window
- TYPE THE URL IN THE WE BROWSER : https://console.aws.amazon.com/?nc2=h_m_mc
- Then enter detail and Sign in then
If you see the message, You must first log out before logging into a different AWS account:
- Choose click here
- Close your browser tab to return to your initial Article window
- TYPE THE URL IN THE WE BROWSER : https://console.aws.amazon.com/?nc2=h_m_mc
- Then enter detail and Sign in then
Task 1: Creating a VPC
In this task, you create a new VPC in the AWS Cloud.
A VPC is a virtual network dedicated to your AWS account. A VPC is logically isolated from other virtual networks in the AWS Cloud. You can launch AWS resources, such as Amazon Elastic Compute Cloud (Amazon EC2) instances, into the VPC. You can modify the VPC's IP address range; create subnets; and configure route tables, network gateways, and security settings.
In the AWS Management Console, on the Services menu, click VPC.
If you see New VPC Experience at the top-left of your screen, ensure New VPC Experience is selected. This lab is designed to use the new VPC Console.
The VPC management console offers a VPC Wizard, which can automatically create several VPC architectures. However, in this lab you will create the VPC components manually.
In the left navigation pane, click Your VPCs.
A list of your VPCs displays. A default VPC is provided so that you can launch resources as soon as you start using AWS. There is also a Shared VPC, which you will use later in the lab. However, you will now create your own VPC.
The VPC will have a CIDR range of 10.0.0.0/16, which includes all IP addresses that start with 10.0.x.x. This range contains over 65,000 addresses. You will later divide the addresses into separate subnets.
Click Create VPC and configure:
Name tag: Lab VPC
IPv4 CIDR block: 10.0.0.0/16
Click Create VPC
Note If these options do not appear, cancel and ensure you clicked Your VPCs in the left navigation pane. Then, click Create VPC again.
In the lower half of the page, click the Tags tab.
Tags are useful for identifying resources. For example, a tag can be used to identify dev/test/production environments or cost centers.
Above the list of VPCs, click Actions and select Edit DNS hostnames.
This option assigns a friendly DNS name to Amazon EC2 instances in the VPC, such as the following:
ec2-52-42-133-255.us-west-2.compute.amazonaws.com
Select Enable.
Click Save changes
Any Amazon EC2 instances launched into the VPC will now automatically receive a DNS hostname. You can also add a more meaningful DNS name (for example, app.company.com) later by using Amazon Route 53.
Task 2: Creating subnets
A subnet is a sub-range of IP addresses within the VPC. You can launch AWS resources into a specified subnet. Use a public subnet for resources that must be connected to the internet, and use a private subnet for resources that are to remain isolated from the internet.
In this task, you will create a public subnet and a private subnet in the Lab VPC, as shown in the following image:

Create a public subnet
The public subnet will be for internet-facing resources.
In the left navigation pane, click Subnets.
Click Create subnet and configure:
VPC: Lab VPC
Subnet name: Public Subnet
Availability Zone: Select the first Availability Zone in the list (Do not choose No Preference.)
IPv4 CIDR block:
Click Create subnet
Note The VPC has a CIDR range of 10.0.0.0/16, which includes all 10.0.x.x IP addresses. The subnet you just created has a CIDR range of 10.0.0.0/24, which includes all 10.0.0.x IP addresses. These ranges may look similar, but the subnet is smaller than the VPC because of the /24 in the CIDR range.
Now, configure the subnet to automatically assign a public IP address for all instances launched within it.
Select ☑ Public Subnet.
Click Actions and select Modify auto-assign IP settings.
Select ☑ Enable auto-assign public IPv4 address.
Click Save
Note Even though this subnet is named Public Subnet, it is not yet public. A public subnet must have an internet gateway, which you will create and attach later in the lab.
Create a private subnet
The private subnet will be for resources that are to remain isolated from the internet.
Use what you have just learned to create another subnet with the following settings:
VPC: Lab VPC
Name tag: Private Subnet
Availability Zone: Select the first Availability Zone in the list (Do not choose No Preference.)
IPv4 CIDR block: 10.0.2.0/23
☑ Note The CIDR block of 10.0.2.0/23 includes all IP addresses that start with 10.0.2.x and 10.0.3.x. This is twice as large as the public subnet because most resources should be kept private, unless they specifically need to be accessible from the internet.
Your VPC now has two subnets. However, it is totally isolated and cannot communicate with resources outside the VPC. You will next configure the public subnet to connect to the internet via an internet gateway.
Task 3: Creating an internet gateway
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in a VPC and the internet. An internet gateway does not impose availability risks or bandwidth constraints on network traffic.
An internet gateway serves two purposes:
To provide a target in route tables to connect to the internet
To perform network address translation (NAT) for instances that have been assigned public IPv4 addresses
In this task, you will create an internet gateway so that internet traffic can access the public subnet.
In the left navigation pane, click Internet Gateways.
Click Create internet gateway and configure:
Name tag: Lab IGW
Click Create internet gateway
You can now attach the internet gateway to your Lab VPC.
Click Actions and select Attach to VPC.
For VPC, select Lab VPC.
Click Attach internet gateway
The internet gateway is now attached to your Lab VPC. Even though you have created an internet gateway and attached it to your VPC, you must also configure the route table of the public subnet to use the internet gateway.
Task 4: Configuring route tables
A route table contains a set of rules, called routes, which are used to determine where network traffic is directed. Each subnet in a VPC must be associated with a route table; the table controls the routing for the subnet. A subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same route table.
To use an internet gateway, a subnet's route table must contain a route that directs internet-bound traffic to the internet gateway. If a subnet is associated with a route table that has a route to an internet gateway, it is known as a public subnet.
In this task, you will do the following:
Create a public route table for internet-bound traffic
Add a route to the route table to direct internet-bound traffic to the internet gateway
Associate the public subnet with the new route table
In the left navigation pane, click Route Tables.
Several route tables are displayed, but there is only one route table associated with Lab VPC. This route table routes traffic locally, so it is called a private route table.
Select the route table that shows Lab VPC in the VPC ID column. (You can expand the column to see the names.)
Hover in the Name column and click the pencil ✏ icon.
Enter a name of Private Route Table and then click the check mark ✔ icon.
In the lower half of the page, click the Routes tab.
There is only one route. It shows that all traffic destined for 10.0.0.0/16 (which is the range of the Lab VPC) will be routed locally. This allows all subnets within a VPC to communicate with each other.
Now, create a new public route table to send public traffic to the internet gateway.
Click Create route table and configure:
Name tag: Public Route Table
VPC: Lab VPC
Click Create and then click Close
Select ☑ Public Route Table, ensuring that it is the only route table selected.
On the Routes tab, click Edit routes
Now, add a route to direct internet-bound traffic (0.0.0.0/0) to the internet gateway.
Click Add route and configure:
Destination:
Target: Select Internet Gateway and then Lab IGW
Click Save routes and then click Close
The last step is to associate this new route table with the public subnet.
Click the Subnet Associations tab.
Click Edit subnet associations
Select the row with Public Subnet.
Click Save
The Public Subnet is now public because it has a route table entry that sends traffic to the internet via the internet gateway.
To summarize, you can create a public subnet as follows:
Create an internet gateway
Create a route table
Add a route to the route table that directs 0.0.0.0/0 traffic to the internet gateway
Associate the route table with a subnet, which therefore becomes a public subnet
Task 5: Creating a security group for the App Server
A security group acts as a virtual firewall for instances to control inbound and outbound traffic. Security groups operate at the instance network interface level, not the subnet level. Therefore, each instance can have its own firewall that controls traffic. If you do not specify a particular security group at launch time, the instance is automatically assigned to the default security group for the VPC.
In this task, you will create a security group that allows users to access the App Server via HTTP.
In the left navigation pane, click Security Groups.
Click Create security group and configure:
Security group name:
Description:
VPC: Lab VPC
For Inbound rules, click Add rule and configure:
Type: HTTP
Source: Anywhere
At the bottom of the page, click Create security group
The inbound rules determine what traffic is permitted to reach the instance. You have configured it to permit HTTP (port 80) traffic coming from anywhere on the internet (0.0.0.0/0).
You will use this application security group in the next task.
Task 6: Launching an App Server in the public subnet
To test that your VPC is correctly configured, you will now launch an Amazon EC2 instance into the public subnet and confirm that the App Server is accessible from the internet.
On the Services menu, click EC2.
At the top-left of the screen, ensure that New EC2 Experience is selected. This lab is designed to work with the New EC2 Console.
Scroll down the page, click Launch instance and select Launch instance.
Configure the following:
Step 1 (Choose AMI)
AMI: Amazon Linux 2 AMI
Step 2 (Choose Instance Type)
Instance Type: t3.micro (If you are unable to launch t3.micro, try using t2.micro. This is because all instance types are not available in all regions/AZs.)
Step 3 (Configure Instance)
Network: Lab VPC
Subnet: Public Subnet
IAM role: Inventory-App-Role
Scroll down to and expand Advanced Details. Copy and paste the following into User data:
#!/bin/bash
# Install Apache Web Server and PHP
yum install -y httpd mysql
amazon-linux-extras install -y php7.2
# Download Lab files
wget https://us-west-2-tcprod.s3.amazonaws.com/courses/ILT-TF-200-ARCHIT/v6.8.26/lab-2-webapp/scripts/inventory-app.zip
unzip inventory-app.zip -d /var/www/html/
# Download and install the AWS SDK for PHP
wget https://github.com/aws/aws-sdk-php/releases/download/3.62.3/aws.zip
unzip aws -d /var/www/html
# Turn on web server
chkconfig httpd on
service httpd start
Step 4 (Add Storage)
Use default settings (no changes)
Step 5 (Add Tags)
Click Add Tag
Key:
Value:
Step 6 (Configure Security Group)
Click Select an existing security group
Select App-SG
Click Review and Launch
You receive a warning that you will not be able to connect to the instance. This is acceptable because you will not be connecting to the instance. All configuration is done via the user data script.
Click Continue
Step 7 (Review)
Click Launch
Select Proceed without a key pair
Select I acknowledge that...
Click Launch Instances
A status page notifies you that your instances are launching.
Click View Instances
Before continuing, wait for the instance state to display running.
Tip To update the display, click the refresh icon occasionally.
Once the instance is running, select App Server.
In the Details tab, copy the IPv4 Public IP address.
Open a new web browser tab, paste the IP address into the address bar, and press ENTER.
If your VPC was configured correctly, you should see the Inventory application and the message Please configure Settings to connect to database. No database settings have been configured yet, but the appearance of the Inventory application proves that the public subnet has been correctly configured.
Note If the Inventory application does not appear, wait 60 seconds and refresh the browser tab to try again. It can take a couple of minutes for the EC2 instance to boot and run the script that installs software.
Challenge: Configure VPC peering
Note This challenge task is optional and is provided in case you have lab time remaining. To skip to the end of the lab, click here.
Another VPC called Shared VPC has been provided as part of this lab. Your task is to create a peering connection between your Lab VPC and the Shared VPC, as shown in the following architecture diagram:
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them privately. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, with a VPC in another AWS account, or with a VPC in a different AWS Region.
A database has already been provisioned in the Shared VPC. Once you have configured VPC peering, you will connect the database to the Inventory application to confirm that the peering has been correctly configured.
Create a peering connection
In the AWS Management Console, on the Services menu, click VPC.
In the left navigation pane, click Peering Connections.
First, create a peering connection, which is the VPC component that links two VPCs together.
Click Create Peering Connection and configure:
Peering connection name tag:
VPC (Requester): Lab VPC
VPC (Accepter): Shared VPC
Click Create Peering Connection and then click OK
When a peering connection is created, the target VPC must accept it. This is because the target VPC might be owned by a different account, or the user creating the peering connection might not have permission to accept the connection for the target VPC. However, in this lab, you will accept the connection yourself.
Select Lab-Peer.
Click Actions and select Accept Request.
Click Yes, Accept and Close
Configure route tables
Now, update the route tables in both VPCs to send traffic from the Lab VPC to the peering connection, as shown in the following image:
In the left navigation pane, click Route Tables.
Select Public Route Table.
You will configure the public route table that is associated with the Lab VPC to send traffic to the peering connection if the destination IP address falls within the range of the Shared VPC.
On the Routes tab, click Edit routes
Click Add route and configure:
Destination:
(This is the CIDR range of the Shared VPC.)
Target: Select Peering Connection and then Lab-Peer
Click Save routes and then click Close
Now, configure the reverse flow for traffic coming from Shared VPC and going to the Lab VPC.
Select Shared-VPC Route Table, ensuring that it is the only route table selected.
This is the route table for the Shared VPC. You will configure it to to send traffic to the peering connection if the destination IP address falls within the range of the Lab VPC.
On the Routes tab, click Edit routes
Click Add route and configure:
Destination:
(The is the CIDR range of the Lab VPC.)
Target: Select Peering Connection and then Lab-Peer
Click Save routes and then click Close
The route tables have now been configured to send traffic via the peering connection when the traffic is destined for the other VPC.
Test the peering connection
A database has already been provisioned in the Shared VPC. You will now test the peering connection by configuring the Inventory application to access that database across the peering connection.
Return to the web browser tab with the Inventory application.
Click Settings and configure:
Endpoint: Paste the Endpoint value shown to the left of the instructions you are currently reading
Database:
Username:
Password:
Click Save
The application should now show data from the database.
This proves that the peering connection is working because the Shared VPC does not have an internet gateway. The only way to access the database is via the peering connection.
Conclusion
Congratulations! You now have successfully:
Created a VPC
Created public and private subnets
Created an internet gateway
Configured a route table and associated it to a subnet
End of Article Please Submit your Review.
1 star = Very dissatisfied
2 stars = Dissatisfied
3 stars = Neutral
4 stars = Satisfied
5 stars = Very satisfied
Your feedback is welcome and appreciated.
If you would like to share any feedback, suggestions, or corrections, please provide the details in our
YouTube Channel : https://youtube.com/c/CodeOn
2 stars = Dissatisfied
3 stars = Neutral
4 stars = Satisfied
5 stars = Very satisfied
If you would like to share any feedback, suggestions, or corrections, please provide the details in our
YouTube Channel : https://youtube.com/c/CodeOn